How to Approach Network Security
While the Internet and networks are growing rapidly, they are also becoming more complex and mission critical. This brings new challenges to the folks who run and manage today’s networks. There has been an integration of network infrastructure that now supports voice, video, and data but at the same time new security concerns are also introduced.
As a matter of fact, no computer system in the world can be completely secure no matter how good the security measures are. Probably the only way to fully secure a computer is to isolate it completely, restricting all physical and virtual access to it. Such a system would not be connected to any network and would probably be stored in a secured vault somewhere with no physical access. Though this compuer system would be completely secure, it would also be completely useless. Usefulness of computers stems from the ability to connect to them and use the resources offered by them. So, the goal of network security is to provide continued access to those resources and, at the same time, preventing any un-authorized or malicious activity from taking place.
Cisco IOS software running on Cisco routers has several built-in security tools that can be used as part of a good overall security strategy. Probably the most important security tool in Cisco IOS software are access control lists (ACL). ACLs can be used to define rules to prevent some packets from flowing through the network. In this chapter, you will learn how you can protect the posterior of your network by deterring the most common threats with features available in Cisco IOS itself.
Cisco also produces an array of specialized security appliances such as the Adaptive Security Appliance (ASA) that companies can use for securing their networks.
The CIA Model
A security model is a framework that that provides guiding principles to make systems secure also meeting industry best practices and regulations. A widely applicable model of network security is the confidentiality, integrity, and availability (CIA) triad. CIA is more like a set of three guiding principles that can be used to secure systems. A breach of any of these three principles can have security consequences.
Figure 8-5 CIA Security Model
Confidentiality
Confidentiality means preventing sensitive information from being seen by anyone who is not authorized to see it. It is the capability to ensure that the required level of secrecy is enforced and information is concealed from unauthorized users. Infromation is a very valuable asset and keeping sensitive information secure is critical for enterprises. That’s why confidentiality is the aspect of security that comes under attack most often by those who want to steal information for their own interests. Encryption is a common technique used to ensure confidentiality of data transferred from one computer to another. For example, when a user is performing an online banking transaction, sensitive information such as account statements, credit card numbers, and passwords must remain protected. Encryption techniques ensure that information is not seen as it is being sent back and forth between the user’s computer and the online bank.
Integrity
Integrity prevents any unauthorized modification of data to make sure information stays accurate. If your data has integrity, you can be sure that it is the actual unchanged representation of the original information and hence can be trusted. A commond type of security attack that compromises the integrity of data is the man-in-the-middle attack. In this kind of attack, the attacker intercepts data as it is in transit and makes changes to it without letting the two communicating entities realize that.
Availability
Availability prevents the loss of access to information and resources and ensure that they are ready for use when they are needed. It is a must to make sure that information is readily available at all times so that requests by authorized users could be fulfilled whenever they come. Denial of service (DoS) is one of several types of security attacks that attempts to prevent legitimate access to information and resources hence compromising the availability of affected systems.
Table 8-1 CIA Model
| Goal | Defined | Example | Methodology |
| Availability | Keeping your network services up and running | DoS Attacks | Auto patch updatesRate limiting |
| Integrity | Prevent data modification | Man in the Middle Attack | Hashing |
| Confidentiality | Secure Data from eavesdropping | Packet capture and replaying | Encryption |
The Secured Enterprise Network
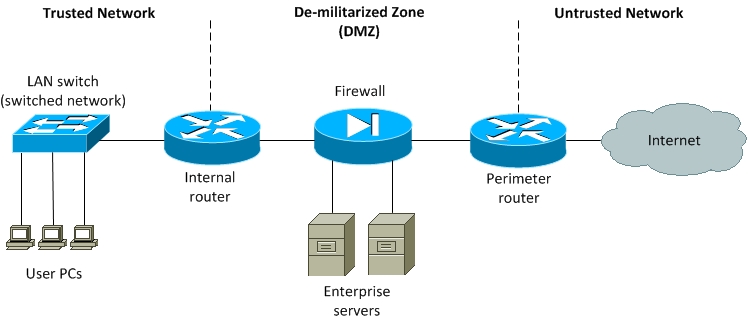
In a medium to large enterprise, the typical secured network is built around a recipe of a perimeter router, a firewall device, and an internal router.
Perimeter Router The perimeter router is the border crossing or the demarcation point between enterprise network resources and the public network, such as the Internet. Therefore, traffic originating from the outside destined for the trusted network or the DMZ must transit through the perimeter router. This router should provide basic security and traffic filtering for both the DMZ and the trusted network.
Firewall The firewall can be a router running the Cisco IOS firewall feature set or a sepcialized device like the Cisco Adaptive Security Applinace (ASA). The firewall can be configured to provide sophisticated controls over traffic flowing between the trusted network, DMZ, and the untrusted network.
Internal Router The internal router provides additional security by providing a point where you can apply further controls to traffic going to or coming from various parts of the trusted network.
Figure 8-1 Secured Enterprise Network
You should do a detailed examination of Figure 8-1 and identify clearly the three distinguishable parts of the network: trusted network, untrusted network, and the demilitarized zone (DMZ).
Trusted Network The trusted network is the internal enterprise network or the corporate local area network (LAN).
Untrusted Network The untrusted network refers to the universe beyond the perimeter router. Typically, the Internet is the untrusted network and is considered highly hostile.
Demilitarized Zone (DMZ) The term DMZ, like many other network security terms, was borrowed from military terminology. In military terms, a demilitarize zone (DMZ) is an area, usually the frontier or boundary between two or more military powers, where military activity is not permitted, usually by peace treaty or other similar agreement. In computer networking, the DMZ likewise provides a buffer zone that separates an internal trusted network from the untrusted hostile territory of the Internet. DMZ is not as secured as the internal network, but because it is behind a firewall, neither is it as non-secure as the Internet. Typically, DMZ hosts services to which access is required from the untrusted network. This includes Web, DNS, email, and other corporate servers that have to be reachable from the Internet.
Classes of Attackers
In the context of this chapter, an attacker refers to someone who attempts to gain unauthorized access to a network or computer system. It is useful to identify different types of attackers and understand their motives in order to be able to characterize attacks and track down such individuals. There are a variety of groups into which attackers are classified and sometimes conflicting views are held by members of the networking community about the definitions of these classifications. Here, I would mention three broad categories:
Hackers Hackers are those individuals who break into computer systems and networks to learn about them, or just to prove their prowess. Some hackers usually mean no harm and do not seek financial gain.
Crackers Crackers are criminal hackers who intend to harm information systems. Crackers usually work for financial gain and are also known as black hat hackers.
Script Kiddies Script kiddies think of themselves as hackers but do not have the needed knowledge and skills. They cannot write their own code; instead, they run scripts written by others to attack systems and networks. As a matter of fact, very sophisticated software tools have become freely available on the Internet which allow novices to execute attacks with point-and-click ease. Today, a very large percentage of wannabe hackers fall in this category.
Vulnerabilities, Threats, and Exploits
Security attacks vary considerably in their sophistication and ability to do damage. As you would learn more about protocols that run today’s networks, you would realize that most security threats are a result of some weakness or inadequacy in the design of the underlying protocol itself. When the Internet was formed, it linked various government entities and universities to one another with the sole purpose of facilitating learning and research. The original architects of the Internet had never anticipated the kind of widespread adoption the Internet has achieved today. As a result, in the early days of networking, security was not designed into network protocol specifications. For this reason most implementations of TCP/IP are inherently insecure. That is a big reason why security is such a burning issue today and in the absence of built-in security mechanisms, we have to rely on additional security measures to make communications secure.
Vulnerability A vulnerability is a weakness in a system or its design that can be exploited by a threat. Vulnerabilities are found in operating systems, applications, and even in network protocols themselves.
Threat A threat is an external danger to the system having a vulnerability.
Exploit An exploit is said to exist when computer code is actually developed to take advantage of a vulnerability. Suppose that a vulnerability exists in a piece of software but nobody has yet developed computer code to abuse it. Because there is no exploit, there is no real problem yet though the vulnerability exists theoretically.
Classes of Attacks
The three major types of network attacks, each having its own specific goal, are as follows:
Reconnaissance Attacks
Reconnaisance literally means the military observation of a region to locate an enemy or to establish strategic features of the region. A reconnaisance attack is not meant to inflict immediate damage to a system or network but only to gather information about the network to prepare for a later attack. It is used to map out the network and discover which IP address ranges are used, which systems are running, and which services or applications reside on those systems. The attacker has to be able to reach a system or network to some extent to perform reconnaisance, but normally no damage is caused at that time. The more common reconnaisance attacks include ping sweeps, port scans, and DNS queries. Here are a few examples of reconnaisance attacks:
Infromation Lookup A network intruder can use tools such as the nslookup and whois in order to determine the IP address space assigned to an organization. Finding a target IP address is one of the first steps in reconnaisance. Once an IP address range is known, an intruder can look for hosts that are alive using ping sweeps. Finally, port scanning can be used to find out which services or applications are running on those live hosts.
Ping Sweeps A ping sweep is a scanning technique used in the reconnaisance phase of the attack, to determine live hosts or computers in a network. A ping sweep sends ICMP echo requests to multiple hosts one after the other. If a certain address is live, it will return an ICMP echo reply confirming its existence.
Port Scans Port scanning is a method used to enumerate what services and applications are running on a system. An intruder sends random requests on different ports and if the host responds to the request, the intruder gets confirmation that the port is active and the associated service or application is listening. The attacker can then proceed to exploit any vulnerabilities by targeting active services. A port scanner is a piece of software designed to search a network host for open ports. Ping sweeps and port scans are two primary reconnaisance techniques used to discover hosts and services that can be exploited.
Packet Sniffers A packet sniffer is a software program that uses a wired or wireless network interface card (NIC) in promiscuous mode to capture all network packets that are sent across a particular collision domain. Promiscuous mode is a mode in which the network interface card sends all packets received on the network to an application for processing. You may recall that, a network interface card would normally send only frames addressed to the MAC address of the card or broadcast / multicast frames to an application while all other frames are simply ignored. There are legitimate applications of network sniffers in troubleshooting and network traffic analysis. However, there are several network applications like Telnet, FTP, SMTP and HTTP that send data in clear text. A packet sniffer can capture all data these applications send including sensitive information, such as user names and passowrds. Packet sniffing is essentially eavesdropping and the information gathered can be used to execute other attacks.
Access Attacks
An access attack is meant to exploit a vulnerability and gain unauthorized access to a system on the network. The information gathered by reconnaisance attacks is used to execute an access attack. When unauthorized access is gained, the attacker can retrieve, modify, or destroy data as well as network resources including user access. Even worse, the attacker can plant other exploits on the compromised system that can be used later to gain access to the system or network with relative ease. Some examples of access attacks are detailed below.
Password Cracking Password cracking is very attractive for attackers as passwords are used to protect all kinds of information including online bank accounts. Password attacks can be accomplished using several methods, including brute forcers, Trojans, IP spoofing, and packet sniffers.
Man-in-the-middle Attacks The man-in-the-middle (MITM) attack, also known as TCP hijacking, occurs when an intruder intercepts communication between two points and can even modify or control the TCP session without the knowledge of either party. TCP hijacking affects TCP based applications such as Telnet, FTP, SMTP (email), or HTTP (Web) sessions.
Trojans A Trojan or Trojan horse is a malicious program that is hidden inside another useful application. Trojans are seemingly harmless programs that hide malicious programs such as a key logger that could capture all keystrokes including passwords, without the knowledge of the user. The term Trojan Horse has originated from the hollow wooden statue of a horse in which a number of Greeks are said to have concealed themselves in order to enter and conquer the ancient city of Troy.
Key Logger A key logger is a tool designed to log or record every single keystroke on the target computer, in a covert mannger so that the person using the keyboard is unaware that their actions are being monitored. All kind of infromation including sensitive information like password has to be basically typed on a computer. Key loggers can log and store all such information on the same computer which can either be retrieved manually or sent as an automated email by the key logger itself. Keyloggers can be both software and hardware based. Several financial institutions use on-screen keyboards for online access to customer accounts as a precaution against keyloggers.
Trust Exploitation The goal of trust exploitation attack is to compromise a trusted host, so that it could be used to stage attacks on other hosts in a network. Typically hosts inside the network of an enterprise are protected by a firewall placed at network boundary. So it is difficult to attack these internal hosts from outside. But these hosts are sometimes made accessible to a trusted host outside the firewall for legitimate purposes. If this trust outside host is compromised, it can be used to attack the inside hosts with relative ease.
Port Redirection A port redirection attack is a kind of trust exploitation attack that uses a compromised but trusted host to pass traffic through a firewall that would otherwise be blocked. Outside hosts can legitimately reach the DMZ and hosts in the DMZ can legitimately reach both inside and outside hosts. If an attacker is able to compromise a host in the DMZ, he could install software to redirect traffic from the outside host directly to the inside host. This would result in outside host gaining illegitemate access to inside hosts without violating the rules implemented in the firewall. An example of a utility that can provide this type of access is netcat.
Rootkits The term rootkit is made up of the word root which is the traditional name of the privileged account on Unix / Linux operating systems, and the word kit which refers to the software components that implement the tool. When a malicious software providing unauthorized access is installed on a system, it is also important to hide the existence of such software to enable continued privileged access. A rootkit is designed to do just that: hiding the existence of certain processes or programs from normal methods of detection. An attacker can install a rootkit when they have obtained root or administrator access to the target system as a result of a direct attack.
Viruses A virus is a malicious software program or code that can cause damage to data or other programs on the target system.
Worms A worm is similar to a virus but it is capable of self-replication increasing the scope of its damage. Worms actually are viruses that can reside in the active memory of a system and can self-replicate and self-propagate from one computer to another over the network.
Buffer Overflows Buffers are locations in computer memory that are used to temporarily hold data and code. A buffer overflow occurs when a program attempts to store data in a buffer, but data is larger than the size of the allocated buffer.
IP Spoofing IP spoofing happens when an intruder attempts to disguise itself by pretending to have a source IP address of a trusted host in order to gain access to resources on a trusted network. Using an IP address of another known host or known network, the attcker attempts to send and receive traffic on the network. The attacker is then able to use network resource that are associated with that sepcific IP address. Once the attcker has got access with IP spoofing, he can use this access for many purposes.
Address Resolution Protocol (ARP) Spoofing ARP spoofing occurse when an attacker tries to disguise its source MAC address to impersonate a trusted host. Address Resolution Protocol (ARP) is used to map IP addresses to MAC addresses residing on one LAN segment. When a host sends out a broadcast ARP request to find the MAC address of a particular host with known IP address, an ARP response comes fronm the host whose IP address matches the request. The ARP response is stored by the requesting host. An attacker can abuse this mechanism by responding as though they are the requested host.
Denial of Service (DoS) Attacks
A Denial of Service (DoS) attack is designed just to cause an interruption to a system or network temporarily, denying access to legitimate users. This interruption in turn can cause loss of money and reputation by preventing customer access to online services. These attacks usually target specific services and attempt to overwhelm them by making numerous requests concurrently. If a system is not protected to react to a DoS attack, it can be easily brough down by running scripts that generate a very large number of requests. Some examples of Denial of Service (DoS) attacks are detailed below.
Distributed Denial of Service (DDoS) It is possible to greatly increase the impact of a DoS attack by launching the attack from multiple systems (botnets) against a single target. This scaled up version of DoS is referred to as a distributed DoS (DDoD) attack. Web servers are a popular target of DDoS attacks and DDoS attacks against companies like online retailers and Web portals keep making news headlines from time to time.
TCP SYN Attack Transmission Control Protocol (TCP) is a popular transport protocol used by several applications including Web based services. TCP is a connection oriented protocol that uses a three-way handshake to establish a TCP connection before application data exchange starts to take place. TCP SYN attack occurs when a host sends a large number of TCP/SYN packets to the target system. Each TCP SYN packet is handled like a connection request, causing the server to send back a TCP/SYN-ACK to acknowledge the connection request also maintaining the state of this connection. The server now waits for the third packet in TCP handshake from the host initiating the connection. However, because it is not a legitimate host that initiated the connection, the third packet needed to complete the TCP handshake never arrives. These half-open connections exhausts the resources at the server, keeping it from responding to connection requests from legitimate users.
Smurf Attack A smurf attack occurs when the broadcast address of a network is used to send packets to all hosts on that network. If network devices are not configured properly they allow such packets to be forwarded till they reach the target network. In such an attack, the attacker will send a large number of IP packets with spoofed IP address of one of the legitimate hosts on the target network. As a result all hosts on the network receiving the broadcast would respond by a unicast sent to the spoofed local IP address. This would cause a large number of packets sent to that hosts essentially resulting in a DoS attack on that host.
Security Threat Mitigation
Several vendors such as Check Point, Juniper, Palo Alto Networks, McAfee, Fortinet and last but not least, Cisco provide hardware and software solutions to mitigate security threats. Cisco offers a specialized yet versatile security product called the Adaptive Security Appliance or ASA, which I believe is one of the best products in its class. A Cisco ASA device is a standalone hardware security appliance. Depending on model, they are quite expensive too. Currently they are beyond the scope of the CCNA Routing and Switching exam.
Fortunately, Cisco Integrated Services Routers (ISRs) like 800, 1800, 2800, and 3800 series and the second generation (G2) of ISRs like 1900, 2900, and 3900 series also have many of the same features that are available on the Cisco ASA devices. These features are bundled as feature sets in the Cisco IOS Software that runs on these routers and include IOS Firewall, IPSec VPN, Intrusion Prevention System (IPS), and Content Filtering to mention a few. For small businesses and enterprise branch offices, where customers are not willing to invest in a dedicated security appliance, Cisco IOS can provide much of the same functionality without additional cost.
Another basic but very powerful security tool available on Cisco IOS are the access control lists (ACLs). We will take the time to cover ACLs in great depth, in the relevant chapter of this book, learning how to create and use them to mitigate security threats.
Physical and Administrative Security Measures
The facility or physical location where devices are housed is in most cases the first and last barrier encountered by an intruder. Physical security prevents intruders from gaining physical access to the devices, and this means hands-on contact. Physical security is even more important that network security but is often overlooked by network administrators. Despite all the high level security measures, a compromise in physical access will almost always result in a complete compromise. Having a secured physical facility that is accessibl only to authorized personnel is extremely important.
While trying to secure a network environment with technical measures, it is equally important to put physical and administrative security measures in place. Some examples of physical security measures are:
- Locks
- Biometric access systems
- Security guards
- Intruder detection systems
- Safes
- Racks
- Uninterruptible power supplies (UPS)
- Fire suppression systems
- Positive air-flow systems
Many security incidents emerge from the inside of the enterprise caused by employees either deliberately or un-knowingly. Policy and procedure driven administrative security measures can be effective against these threats. These administrative controls that help with information security are usually documented in the human resources (HR) department. Some of these measures are:
- Security awareness training
- Security policies and standards
- Change control mechanisms
- Security audits and tests
- Good hiring practices
- Background checks for employees and contractors
For example, if an organization has strict hiring practices that require drug testing and criminal background checks for all employees, the organization will likely hire fewer individuals of dubious character. With fewer people of dubious character working for the company, it is likely that there will be fewer internal security incidents. These administrative measures do not ensure that no security incidents would take place, but they are an important part of an information security program are often utilized especially by large organization.