In order to appreciate the need for virtual LANs, let’s consider how LANs would be built without switches using hubs only. As you are aware hubs are layer 1 devices without any intelligence and they typically relay the frame received on one port to all other ports regardless of the type of frame. As a matter of fact they don’t care what the content of the frame is and the same treatment is given to unicast, multicast, and broadcast frames. As a result, the set of devices connected to a hub are in the same collision domain which means two devices connected to a hub cannot transmit at the same time without causing a collision. The Carrier Sense Multiple Access / Collision Detection (CSMA/CD) mechanism of Ethernet is at work in networks built with hubs. As all devices are in the same collision domain there is performance degradation as more and more devices are connected to the same hub and more collisions start to take place.
Let’s assume we have five physical LANs in our organization: Engineering, Finance, Management, Marketing, and Sales each belonging to one department that need to be connected to the same router which provides Wide Area Network (WAN) connectivity. Here is how this network can be built using hubs alone.
Figure 7-4 Physical LANs
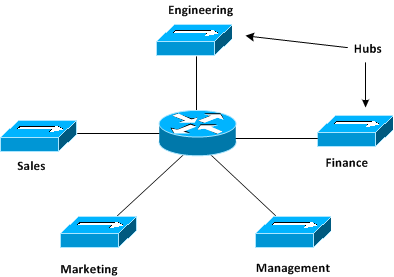
Please note that enterprise networks do not use hubs any more and are built exclusively with switches. But analyzing the above network built with hubs would enable us to appreciate the benefits switches bring. First there is one hub for each physical LAN and all devices in that physical LAN are cabled to the same hub while each hub itself is connected to a separate interface on the router. Also, there is one IP subnet for each physical LAN and any device that is connected to that LAN has to have an IP address in that IP subnet. The router interface on a certain physical LAN also has an IP address in the IP subnet for that LAN. The hosts in the physical LAN have the router’s IP address set as their default gateway. In this design, if you need to add another device in a physical LAN say Engineering, you simple connect it to the Engineering hub and assign it an IP address from the IP subnet for Engineering LAN.
There are some shortcomings in this design. First there are limitations on where you can physically place devices on a certain LAN due to the limited maximum cable length supported by Ethernet cabling standards. Let’s assume there is a new employee in the Engineering department that needs to be connected to the Engineering LAN but there is no physical space in the Engineering department to make room for the new employee. There is plenty of space in the Sales department and the new Engineering employee is made to sit in the Sales department instead. Now, the Sales department is located in another corner of the building and it is not possible to connect the new Engineering employee to the Engineering hub due to the simple fact that the distance exceeds the maximum cable length permissible. The new Engineering employee is instead connected to the Sales hub but this has some undesirable side effects. The Engineering employee is now on the Sales LAN and he can access all resources on the Sales LAN like servers which are meant to be visible only to the Sales people. It is a security issue as organization policies may prevent employees from other departments to have access to Sales documents and data. Also the new Engineering employee would be cut off from resources on the Engineering LAN which may prevent him from effectively doing his job. In the coming sections we will see how virtual LANs in networks built with switches instead of hubs provide means to prevent problems like this yet enabling physical mobility. The design I just described, though obsolete today, has worked well for several years despite its limitations.
In an Ethernet LAN, a set of devices that receive a broadcast sent by any other device is called a broadcast domain. We just learnt in the last section, a switch simply forwards all broadcasts out all interfaces, except the interface on which it received the frame. As a result, all the interfaces on an individual switch are in the same broadcast domain. Also, if a switch connects to other switches too, the interfaces on those switches are also in the same broadcast domain. On switches that have no concept of virtual LANs (VLANs), the whole switched network is one large flat network comprising a single broadcast domain.
A VLAN is simply a subset of switch ports that are configured to be in the same broadcast domain. Switch ports can be grouped into different VLANs on a single switch, and on multiple interconnected switches as well. By creating multiple VLANs, the switches create multiple broadcast domains. By doing so, a broadcast sent by a device in one VLAN is forwarded to all other devices in that same VLAN; however the broadcast is not forwarded to devices in the other VLANs. VLANs provide bandwidth efficiency because broadcasts, multicasts and unknown unicasts are restricted to individual VLANs and also provide security as a host on one VLAN cannot directly communicate with a host on another VLAN.

Because a trunk link can transport many VLANs, a switch must identify frames with their associated VLANs as they are sent and received over a trunk link. Frame identification assigns a unique user-defined number to each frame transported over a trunk link. This VLAN number is also called VLAN ID and as each frame is transported over a trunk link, such unique identifier is placed in the frame header. As each switch along the way receives these frames, the identifier is examined to determine to which VLAN the frames belong and then is removed. VLAN ID field contains a 15-bit value and as such the range of possible VLAN IDs is 0 – 4095. The VLAN IDs of 0 and 4095 are not used and the usable range of VLAN IDs hence is 1 – 4094. By default, all ports on a Cisco switch are assigned to VLAN 1. VLAN 1 is also called the management VLAN and control plane traffic belongs to VLAN 1.
Best practices recommended by Cisco dictate using a separate IP subnet for each VLAN. Simply put, devices in a single VLAN are typically also in the same IP subnet. Layer 2 switches forward frames between devices on the same VLAN, but they do not forward frames between devices in different VLANs. In order to be able to forward frames between two different VLANs, you need a multilayer switch or a router. We will cover this in more detail in a later section of the chapter.
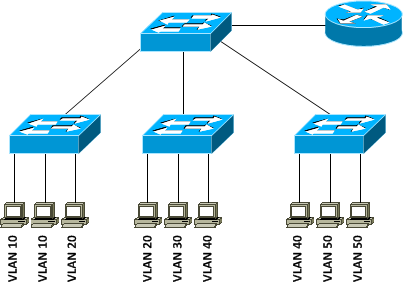
Now, let’s see how we can build the same network using switches instead of hubs and what benefits switches bring to us. Table 7-1 lists VLAN IDs corresponding to organizational departments and IP subnets associated with each VLAN. There is a different IP subnet assigned to each VLAN and if you look carefully the third octet of the IP subnet number is the same as the VLAN ID. It is just an arbitrary number to make the design easily understandable and let us focus more on concepts rather than specific numbers used. The router has a Wide Area Network (WAN) connection and it provides two important functions: WAN connectivity and inter-VLAN routing to enable communication between two different departments or VLANs. As you can see in Figure 7-6, devices belonging to VLANs 20 and 40 are connected to more than one switch. VLANs remove the restriction of having to connect devices belonging to the same LAN to the same device while still providing traffic isolation at layer 2. In yet other words, VLANs can span multiple switches with switch ports belonging to same VLAN existing on different switches. This is one of the several benefits switches bring to local area networks. Also if we want to add another device to say the Engineering VLAN and we want to locate the new user at a location different than the Engineering department, it can simply be accomplished by connecting the new device to the nearest switch and assigning the switch port to the Engineering VLAN. Compare it with the similar situation in the network built with hubs and you would be able to appreciate that network becomes more flexible without sacrificing security or traffic isolation. The router provides inter-VLAN routing in this scenario but the same functionality can also be achieved by using a layer 3 switch like the Cisco 3560.
Table 7-1 VLANs Corresponding to Organizational Departments
| VLAN IDs | Names | IP Subnet |
| 10 | Engineering | 192.168.10.0/24 |
| 20 | Finance | 192.168.20.0/24 |
| 30 | Management | 192.168.30.0/24 |
| 40 | Marketing | 192.168.40.0/24 |
| 50 | Sales | 192.168.50.0/24 |
Figure 7-6 Switches Using VLANs Remove Physical Boundaries
VLAN Membership
One of the tasks that a system administrator has to perform while creating VLANs is to assign switch ports or interfaces to each VLAN. There are two ways switch interfaces can be assigned to VLANs and this gives rise to two different types of VLANs: static and dynamic. In the case of static VLANs, each switch port is statically assigned to a specific VLAN and any host connected to that switchport would automatically be a part of that VLAN. This kind of VLANs is static because individual switch ports are permanently allocated to specific VLANs. VLANs in this case are tied to switch ports and not to what is connected to those switch ports. In the case of dynamic VLANs however, all the host devices’ hardware addresses are assigned into a database so the switch can be configured to assign VLANs dynamically any time a host is connected to a switch. In this case VLAN is tied to the hardware addresses or MAC addresses of hosts and not to switch ports. A host whose MAC address is tied to a certain VLAN would be part of that VLAN regardless of which switch port it is connected to. Static VLANs are easier to create than dynamic VLANs because there is no need to document the hardware addresses of all hosts that would possibly be connected to the LAN and then to store them in a database on the switch. I will cover both static and dynamic VLANs in the coming sections.
Static VLANs
The most common and straightforward method to create VLANs is static VLANs and these are also more secure than dynamic VLANs. The security hinges on the fact that VLANs are manually associated to switch ports by switch configuration and these VLAN associations are always maintained unless the port assignment is manually changed.
Static VLAN configuration is pretty easy and it works really well in most enterprise networking environments where user mobility is limited and controlled. End points typically consist of desktop computers, printers and servers which are permanently cabled to switch ports. It is fitting to associate VLANs to switch ports in such an environment.
Dynamic VLANs
Dynamic VLAN bases VLAN assignment on hardware (MAC) addresses, protocols, or even applications that create dynamic VLANs. Let’s consider a specific case where MAC addresses have been entered into a centralized VLAN management application and you connect a new node to a switch. If the node is attached to an unassigned switch port, the VLAN management database can look up the hardware address and both assign and configure the switch port into the correct VLAN. This makes configuration and management a lot easier because if a user moves to a new location and plugs the node into a new switch port, the switch simply will assign them to the correct VLAN automatically. It is possible because VLAN assignment is tied to hardware addresses of nodes rather than physical switch ports. But this ease of VLAN management and user mobility comes at a cost: you have to do a lot more work initially noting the hardware addresses of all nodes that are supposed to be connected to the LAN and set up the VLAN database accordingly.

