Encryption is the fundamental mechanism used to secure communications and is at the heart of any type of VPN implementation. Encryption obscures information to make it unreadable to unauthorized recipients. It provides a means to secure communications over an insecure medium such as the Internet. Let’s now establish the definitions of some basic terms:
- Plaintext: The original data before encryption is known as plaintext.
- Ciphertext: The data after encryption is called ciphertext.
- Hash: A hash, or hash value, is a binary number generated from original data by applying a mathematical formula. Hash is a value calculated from the original data to uniquely identify the data.
- Encryption: It is the process that transforms plaintext into ciphertext. Encryption involves the use of an algorithmic process that uses a secret key (binary string) to transform plain data into a secret code.
- Decryption: It is the reverse process of encryption that is used to convert encrypted data back into its original form.
Cryptography Algorithms
In general, there are three types of cryptography algorithms:
- Symmetric Key Cryptography: It involves a single key that is used for both encryption and decryption.
- Asymmetric Key Cryptography: It uses a pair of two different keys, one used for encryption and the other for decryption.
- Hash Function: A hash function is a one-way mathematical function that is used to produce a unique hash value from original data. The hash function is not reversible which means that the original data cannot be reconstituted from the hash value even with the knowledge of the hash function. The hash value is usually appended to the original message as the unique identifier of the message like a fingerprint.
In Figure 12-2, we present a very simple encryption algorithm known as the Caesar cipher. This method is named after Julius Caesar, who used it to encrypt his private correspondence. Each alphabet is shifted right or left by a fixed number of positions. The number of positions and the direction of shift must be known to both the sender and receiver in order to encrypt and decrypt the message.
Caesar cipher with a left shift of three positions looks like this:
Plaintext: ABCD EFGH IJKL MNOP QRST UVWX YZ
Ciphertext: XYZA BCDE FGHI JKLM NOPQ RSTU VW
Figure 12-2 Encryption Process
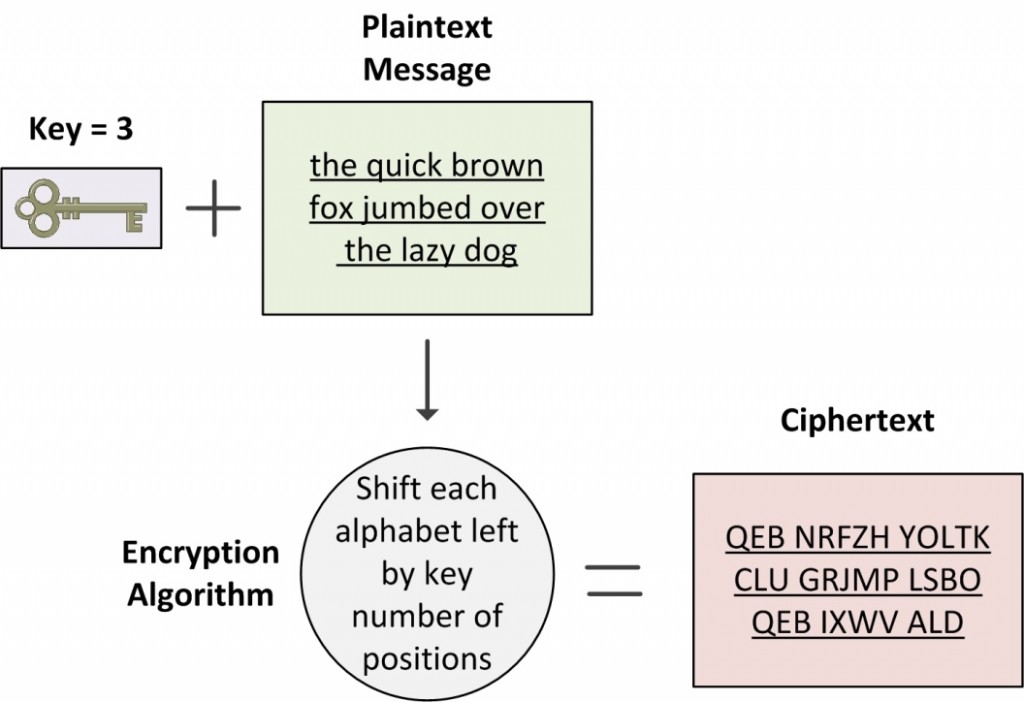
Please keep in mind that today’s encryption algorithms are way more complex than the Caesar cipher and involve complicated mathematical computations that can be performed only by computers. However, the basic principle of encryption is still the same.
Symmetric key cryptography does not require a lot of computational power and therefore is much faster. It is well suited for encrypting large amounts of data such as data transfers over VPN connections. It can also run on network devices even without dedicated cryptography hardware due to being less computationally intensive. It should not be a surprise that symmetric key cryptography is employed by the most popular cryptographic algorithms today namely DES, 3DES, and AES.
- Data Encryption Standard (DES): DES is an old and common cryptographic algorithm. It uses a 56-bit key to encrypt 64-bit data blocks. DES is no longer considered very secure and is not recommended any more. The weakness of the protocol is primarily due to the very short key size of 56-bits.
- Triple DES (3DES): 3DES is an enhancement of DES that employs up to three 56-bit keys (168-bits). It runs three passes of the encryption and decryption process over the same block of data. DES was considered insecure due to its small key length of 56-bits. 3DES was derived from DES mainly to increase the length of key to 168-bits (three times the 56-bit key for DES) without switching over to an entirely new algorithm. 3DES also encrypts 64-bit data blocks just like DES, though it uses a 168-bit key. 3DES is the recommended replacement protocol to use in all DES implementations.
- Advanced Encryption Standard (AES): Advanced Encryption Standard (AES), also known as Rijndael, is one of the most common cryptography algorithms today. The AES is more flexible than both DES and 3DES as it uses a variable data block length as well as key length. It can use any combination of key lengths of 128, 192, or 256 bits and data block lengths of 128. 192. or 256 bits. AES is gradually replacing the predecessor DES and 3DES standards.
The following table provides a comparison of the three encryption algorithms at a glance.
Table 12-1 Encryption Algorithms for VPNs
|
Algorithm |
Key Length (bits) |
Block Length (bits) |
Security |
| DES | 56 | 64 | Insecure |
| 3DES | 168 (3 times 56) | 64 | Relatively secure |
| AES | 128, 192, or 256 | 128, 192, or 256 | Strong |
Asymmetric key cryptography, also known as public-key cryptography, uses a two-key pair: one key is used to encrypt plaintext while the other key is used to decrypt the ciphertext. Each end user has its own pair of public and private keys. The public key of each end user is publicly available via a key management system. The private key is known only to the end user and is never exchanged or revealed to anyone other than the end user.
Asymmetric key cryptography is typically used in the key management process of VPN establishment, though it is not used to encrypt data being computationally intensive. Some of the common asymmetric key algorithms include RSA and Diffie-Hellman.
- RSA: The RSA algorithm derives its name from the surnames of its three developers, Rivest, Shamir, and Adleman. It can be used for key exchange, digital signatures, and message encryption.
- Diffie-Hellman (DH): DH is used for exchanging keys over an insecure medium, between two end users that have no prior knowledge of each other. The secret key obtained through DH can be used to encrypt subsequent messages using a symmetric key algorithm like 3DES or AES. The DH algorithm is used only for secret key exchange.
Hash Functions
A hash function is a mathematical formula used to compute a fixed-length hash value from the original plaintext. A hash function is also known by a number of other names as well including hash algorithm, message digest, and one-way encryption. The original message cannot be reconstituted from the hash value even with the knowledge of hash function. Hash functions are used to create a digital fingerprint of the any type of data that is then appended to the original data. Hash functions provide data integrity ensuring that the information has not been altered during transmission.
We introduce two of the most common hash functions widely used today:
- Message Digest (MD): Message Digest algorithms are a series of hash functions (MD2, MD4, and MD5) that produce a 128-bit fixed-length hash value (also called a message digest or fingerprint) from input data of arbitrary length. We cover MD5 in some detail here. MD5 was developed by Ronald Rivest in 1991. MD5 replaced its predecessor MD4, addressing potential weaknesses in MD4. The MD5 algorithm produces a 128-bit (16-byte) hash value, typically expressed in text format as a 32 digit hex number. Several vulnerabilities have been discovered in the design of MD5 and SHA family of hash functions is recommended as a replacement of MD5.
- Secure Hash Algorithm (SHA): SHA is another series of popular hash functions that produces 160-bit hash value. SHA is slower than MD5 but is more secure. The first member of SHA family was SHA-0 that was introduced in 1993. SHA1 was the successor to SHA-0 that came in 1995 and is the most popular in the SHA family. SHA-1 is considered to be the successor to MD5 and is widely used in a variety of applications including Secure Sockets Layer (SSL) and IPsec.
